Blog
Vennx


Da reação à predição: a evolução inevitável do enterprise risk management
ERM reativo está morto. Descubra como IA, continuous monitoring e predictive analytics transformam GRC.


The silent threat that costs US $8.3 billion to the global market
Third-party risks cost US$8,3 bi per year. Is your management prepared to prevent the next incident?


Intelligent Access Management: The Path to Seamless Audits
Strategic access management is the basis for predictable audits and sound governance.


Why Artificial Intelligence in risk management is no longer optional
EU AI Act, emerging risks and competitive gap: why AI in GRC became a strategic imperative in 2026.


IAM and ITGC in Practice: How we structure living and auditable governance
IAM and ITGC: 21 risks mapped, 26 actions and automated access governance.


How we structured the ideal RBAC for SAP with intelligence and scale
How we built scalable SAP RBAC with SoD and intelligent role mining


Real Case: How We Use AI to Create 20 SoD Arrays in 7 Days
How we use AI to create 20 SoD arrays in 7 days and structure access governance before SAP.
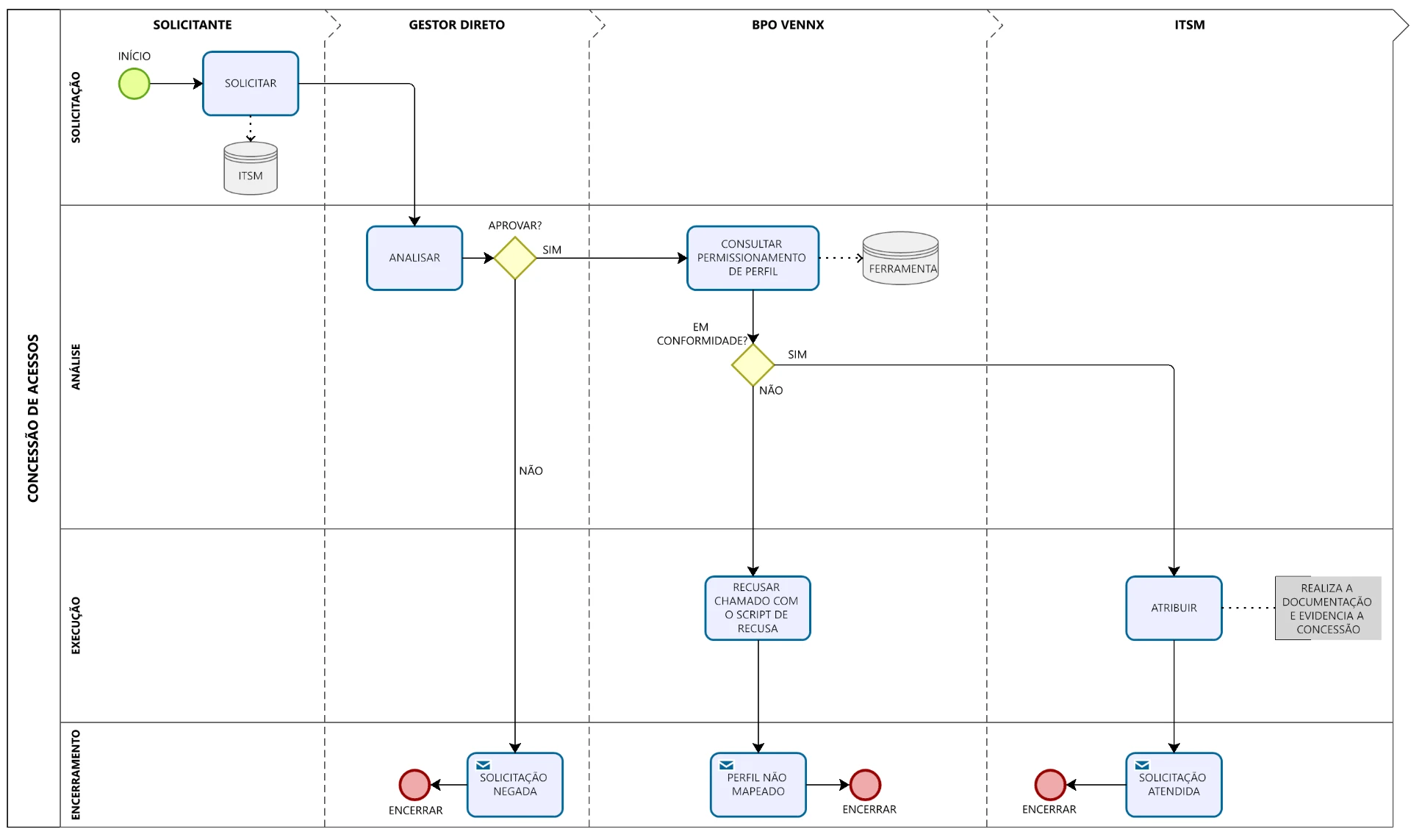

Open Source Vennx: why we opened our access BPO framework
We open our access BPO framework to prove SOX compliance can be transparent, auditable and sustainable.


ITDR and the new frontier of digital security: why the future depends on identity
ITDR redefines security by detecting and responding to identity abuse in real time.


Automated GRC: why 2026 requires a new governance structure
2026 marks the turn from manual GRC to automated GRC, integrated with AI, regulations and strategic decisions.


GRC failures: how the lack of control brought down Will Bank
Will Bank case shows how GRC failures can escalate risks and compromise the continuity of fine institutions


Brazil on the global AI radar: what this breakthrough reveals about the future of corporate GRC
Brazil consolidates as a global reference in AI applied to CRM and corporate governance.


AI for highly regulated environments: when innovation and governance need to evolve together
AI in regulated environments requires governance, traceability and control to generate real value to the RCMP.


Security Culture and AI: The Decisive Moment for 2026
AI is already critical infrastructure. Without governance and mature GRC, risk grows faster than innovation.


Third-party management: the invisible risk that your audit is not seeing
Understand how to eliminate invisible risks.


The new face of risk: how AI can protect your business from supply chain attacks
How AI is protecting companies from invisible risks in the supply chain and third parties.






