How we structured the ideal RBAC for SAP with intelligence and scale

The second stage of transformation: making access as strategic as it is secure
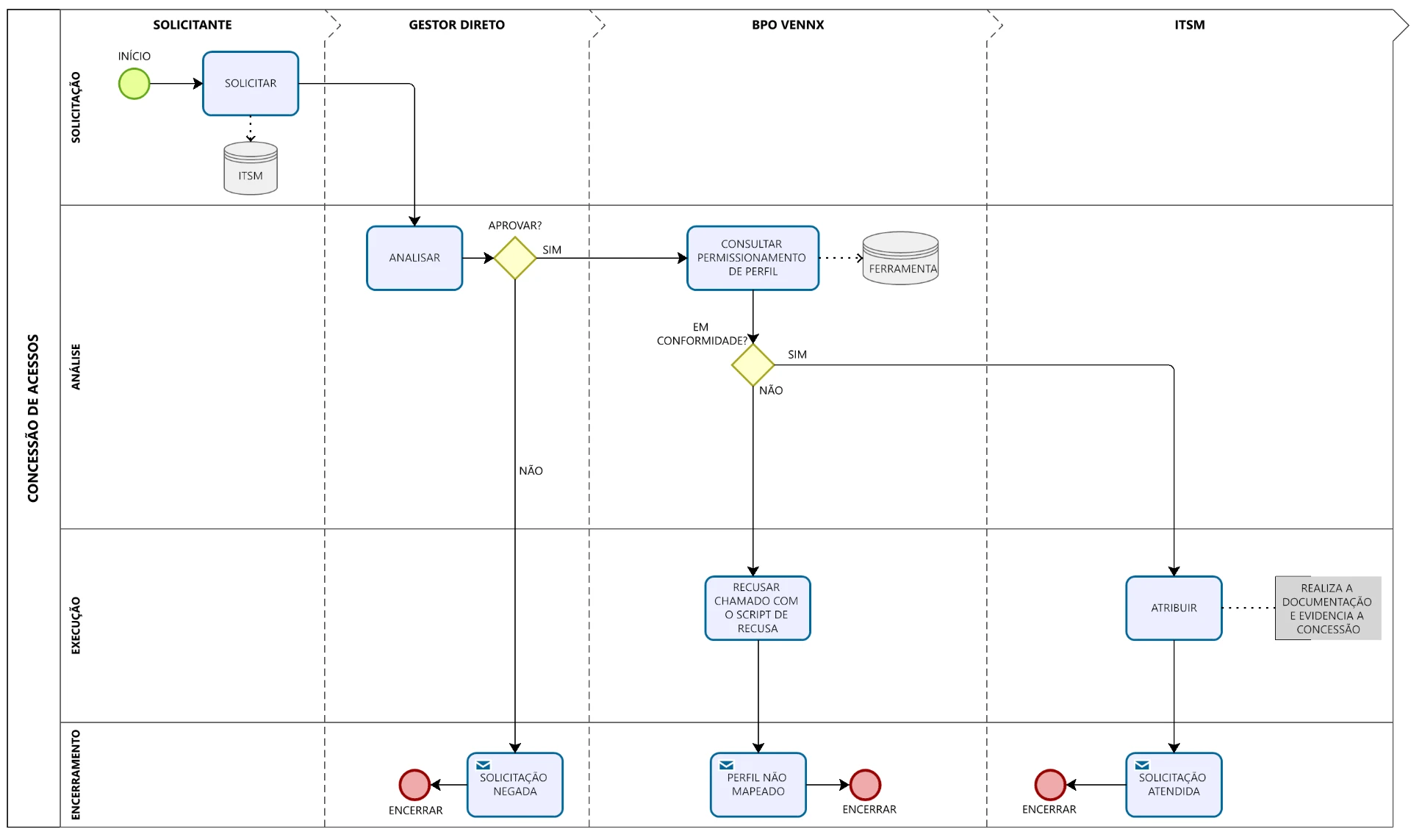
In the second chapter of this journey of governance, we enter into a challenge that, at first glance, may seem purely technical. But in practice, what was at stake was much deeper: how to translate segregation rules into coherent, scalable and auditable operational structures? With this question in mind, we addressed the mission of implementing the RBAC (Role-Based Access Control) model for an emerging SAP environment.
After designing 20 SoD arrays with our proprietary SoD Discovery AI, it became clear that it was not enough to define what needed to be separated. It was necessary to establish how the profiles would be composed in practice. And that process would need to monitor the reality of the positions, the criticality of access and the fluidity of operations.
When old profiles saw risk traps: the legacy that awaited us
The previous environment brought us a classic portrait of how improvisation, over time, compromises any chance of control: profiles created on demand, inconsistent nomenclatures, duplicate permissions and a scenario in which auditing or adjusting became almost impossible.
Therefore, before redesigning any structure, we dive deep into the diagnosis. We identify an accumulation of incompatible functions, profiles granted without standard, absence of role mining, and a complete disconnection between organizational structure and systemic access. The sum of all this was an environment exposed to operational risks, constant reshuffling and serious barriers to compliance.
The intelligence behind architecture: role mining with purpose
Transforming this scenario required methodology, technology and an active listening to real processes. We start with the detailed mapping of the 210 users, divided between positions with and without seniority. Then we went beyond the formal descriptions. We understand what each function actually did, its interactions in the workflow and the critical points where segregation was indispensable.
With this knowledge, we set out for the technical survey: we analyzed 4.821 active Fiori Apps and identified 297 as critical to the business. We cross these data with the 56 risks of the SoD matrix and, from there, we apply our role mining methodology. The goal? Create functional groupings, consistent with business activities and aligned with the principles of least privilege and maximum traceability.
A layered RBAC, designed to grow with the business
With the processed and validated data, we set out to build the model. We have structured RBAC in layers to ensure clarity, modularity and governance from the beginning. Layer 2 grouped non-critical operational transactions, such as routine queries and records. Layer 3, on the other hand, concentrated critical transactions, requiring strict segregation, such as high-value approvals, changes to master data and accounting reversals.
This structure not only facilitated managers' understanding of the profiles, but also enabled more effective periodic reviews, rapid responses to organizational changes and a significant gain in the quality of internal and external audits. All this within a model that can evolve with the growth of SAP, without losing control or visibility.
Real Transformation Happens When Control Turns Culture
More than a technical delivery, this stage consolidated a new culture of governance. What was once impromptu became the norm. What was obscure gained traceability. And what seemed complex, became manageable. This transformation in SAP, driven with strategy, analysis and technology, paved the way for access management that not only protects, but also accelerates business.
Today, with the RBAC model active and validated, the client has not only a safer environment, but also a permissions structure aligned with the actual operation and prepared to face audits, extensions and changes with agility.
If your company also faces the challenge of migrating, restructuring or auditing your SAP accesses, talk to a Vennx expert. We have proprietary technology, proven experience and a method that guarantees clarity from the first click.
Posts Relacionados
Informação de valor para construir o seu negócio.
Leia as últimas notícias em nosso blog.