Open Source Vennx: why we opened our access BPO framework
The market needs transparency, and we went further
There is a lot of talk about good practices, but little is shared about what really works. At Vennx, we decided to do something different: we opened the entire structure that we use in access management projects with SOX compliance requirements. We are not talking about a generic whitepaper or an illustrative flowchart, but an operational, technical and functional set that supports the daily operation of companies audited by Big4.
Our open source framework delivers not only the paths, but the tools. From the first steps of mapping the current environment to the assisted transition to a sustainable access BPO model, everything was included. And, above all, this reflects our belief that GRC cannot be a black box, it needs to be enforceable, auditable and replicable.
BPO as an extension of corporate intelligence
Third-sourcing has long ceased to be a cost solution. When we talk about access management within regulated environments, such as those following SOX, we are dealing with much more than operation: we are talking about trust, traceability and efficiency. BPO, in our understanding, does not replace the company, it acts as a parallel intelligence, responsible for keeping flows alive, testable and aligned with internal policies and monitored risks.
The framework we open contemplates this logic. We built the foundation from a faithful AS IS model, validated in the field, and evolved to a TO BE designed with multidisciplinary times. Consulting, technology and operation go hand in hand. This connection ensures that the proprietary technology we apply to our customers is not only efficient, but that it is 100% aligned with the strategic vision of the business.
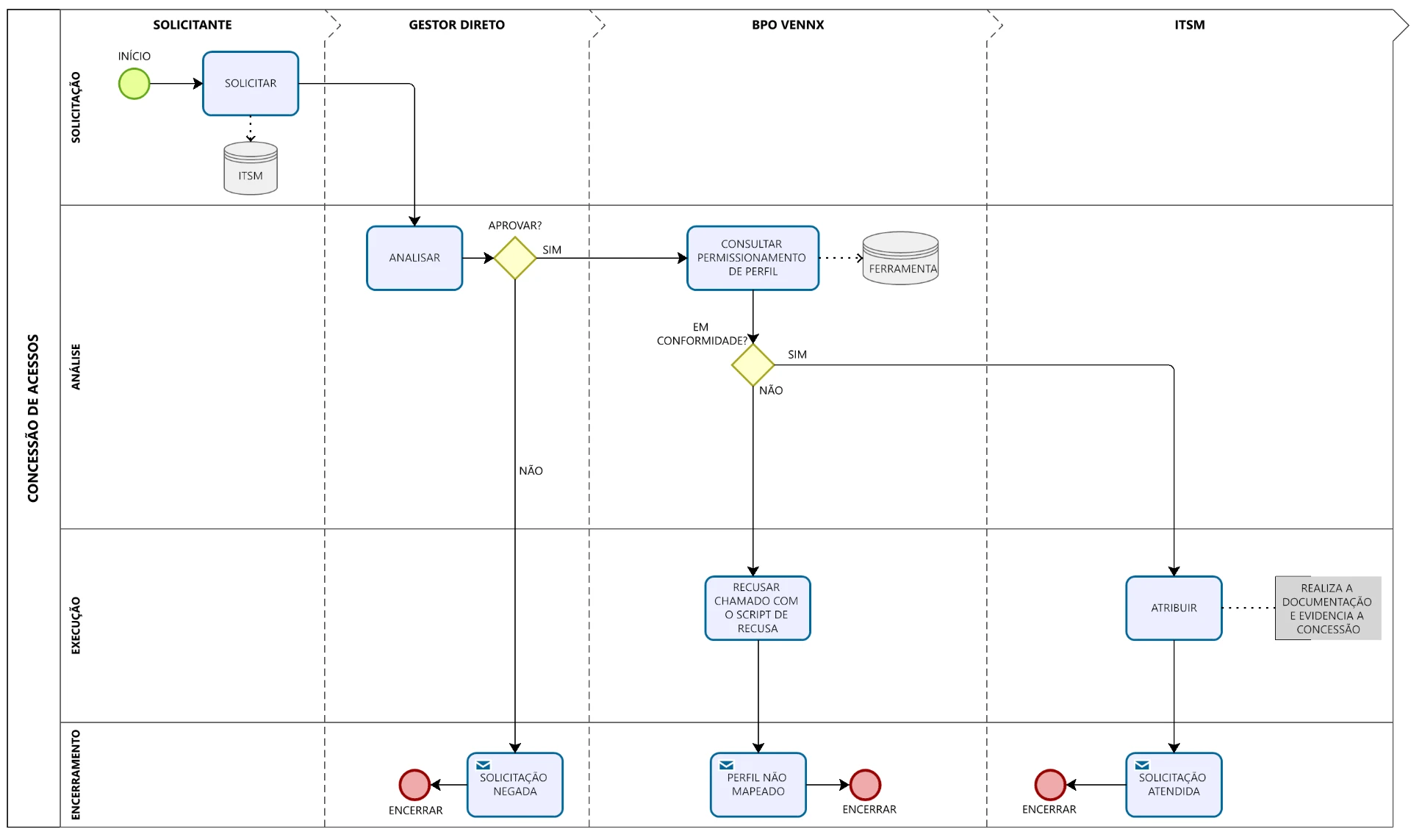
Inside the Vennx Access BPO Model
Our methodology starts with the actual analysis of the current environment. There are no shortcuts. First, we identify all the stages, systems and interfaces that make up the access journey within the company. In parallel, we activate the GRC eye to track risks and points of failure. This stage is essential so that the TO BE process is not an idealization, but a viable evolution.
With this consolidated mapping, the team enters a period of assisted operation. From there, Vennx and customer professionals work side by side. The goal is to validate the new model as it happens. That is, at the same time that we execute the calls, we structure the routines and we understand the throats in real time. This is a key point: TO BE is born from the field, not from theory.
In the case of Brazil’s largest battery manufacturer, for example, it was precisely this structure that made it possible to exceed the SLA goals. This is because we deliver not only automation and scripts, but a continuous support model that accompanies the maturation of the operation.
Aggressive, but possible SLAs
It is common to find resistance to the idea that a BPO can operate with high-demand SLAs, especially in complex and multi-system scenarios. However, our operation proves the opposite. We work with an average of more than 120 calls per day, with resolutions within business hours and without emergency escalations.
This performance does not happen by chance. It is supported by elements such as: standardization of flows, automation of decisions, templates parameterized by system (such as JDE), and a detailed governance on each exception treated. This degree of control and agility is only possible because our model starts from the field, but also because of the way we understand IAM, segregation of functions and the impacts that each concession generates on the whole.
Risks under control and naturalized compliance
Access management is one of the most delicate points in any audit. Either by granting without criteria, by the absence of history, or by conflicts of profiles. Our framework helps to solve all these points, based on three main pillars:
- Each action is recorded, with traceability and context;
- Approvals follow formal heights and are linked to defined roles;
- The SOD/SAT matrix guides the automatic validation of risks, even if the process is under construction.
This structure allows us to meet with peace of mind the requirements of SOX, but also of internal standards and good practices of GRC. And, above all, it offers security for the business. This security that was designed, documented and is now available for other times.
Adaptable, replicable and scalable
Our model was designed to grow with customers. Each new process is documented replicably, ready to be adapted to other units, systems or subsidiaries. Integrations with corporate policies are also part of the design, from access rules to compliance and benefits management standards.
And that is why our delivery is not only technical. It's strategic. It allows internal time to keep the focus on governance and risk analysis, while Vennx runs the flow with discipline, autonomy and traceability. The result is a BPO that does not overload, but strengthens internal control.
Code, logic and method, all open
We opened up what has always been our differentiator: the way we think, model and operate access management in critical environments. What used to be a black box is now public. We include flows, checklists, scripts, approval logic and best practices that we apply in the field. And not as a concept, but as a functional package that you can adapt and roll.
All because we believe in a more technical, collaborative market and less biased by closed solutions. The opening is not just a showcase, it is an invitation.
If you lead or support areas of security, GRC or technology, that content was made to be used, audited and evolved.
Download now the e-book with our complete access BPO framework and see how to apply in your company: https://forms.office.com/r/iZ8pLFvfS8
Posts Relacionados
Informação de valor para construir o seu negócio.
Leia as últimas notícias em nosso blog.


Real Case: How We Use AI to Create 20 SoD Arrays in 7 Days
How we use AI to create 20 SoD arrays in 7 days and structure access governance before SAP.




