Failed access management and hidden risks: what the Coupang case reveals about ex-employees and critical gaps in GRC

The silent danger of unrevoked access.
The recent data leak at Coupang, the South Korean digital marketing giant, has made public one of the most underestimated risks by companies: the persistent access of former employees to critical systems.
After leaving the company, a former developer maintained access to an internal authentication key. For months, he freely browsed sensitive databases, undetected. The result: data from virtually every adult in South Korea was compromised, an operational, legal and reputational disaster.
This failure, far from being punctual, exposes a recurring blind spot in large companies: the absence of automated and continuous processes for revocation of access. The problem is not technical, it is governance. And its impact goes far beyond IT.
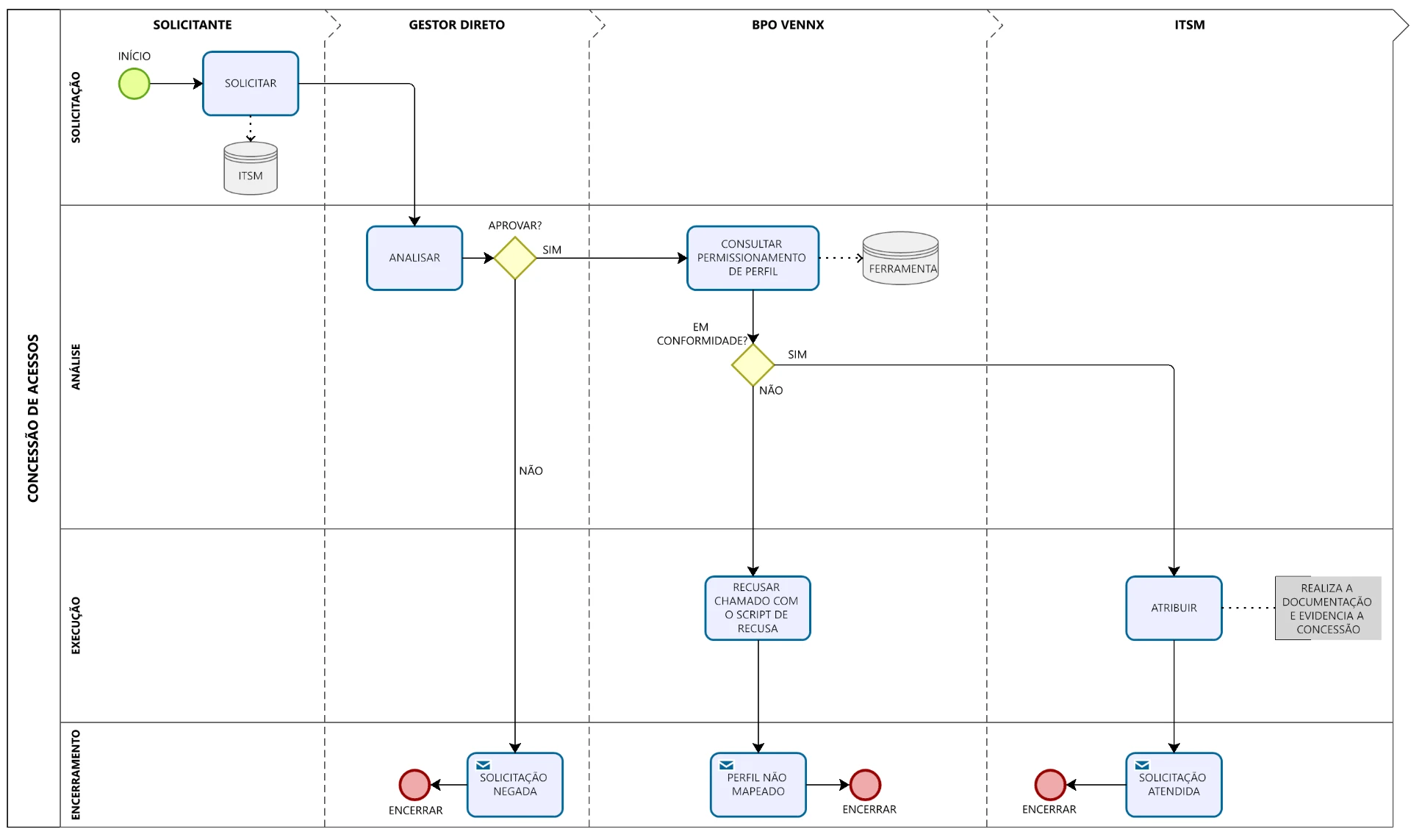
IAM (Identity and Access Management) is no longer an auxiliary function, it is one of the central structures of any GRC strategy. The absence of real-time audit trails, coupled with the lack of dynamic credential correction, makes the corporate environment vulnerable to internal risks, even after the end of an employment relationship.
That is why solutions like Oracle, developed by Vennx, become indispensable, being possible to continuously audit permissions, identify obsolete accesses, cross data between systems and correct faults automatically, aligning compliance with SOX, ISO27001 and LGPD.
The Coupang case is a global alert. Former employees should not pose operational risks. But without automation and living governance, any forgotten credential can become the next headline.
Mature companies need to treat access management as a strategic infrastructure not as a technical or bureaucratic function. Control needs to be granular, intelligent and live. Because the threat, many times, has already gone out the door... but it's still inside the system.
Posts Relacionados
Informação de valor para construir o seu negócio.
Leia as últimas notícias em nosso blog.


Real Case: How We Use AI to Create 20 SoD Arrays in 7 Days
How we use AI to create 20 SoD arrays in 7 days and structure access governance before SAP.